Featured
Table of Contents
7 Best Vpns For Tor Browser In 2023 (Do You Need One?)
Nevertheless, this is most likely just to be advised if you are a highly sophisticated online user. Your browsing history and cookies are automatically reset when you stop utilizing it. Tor avoids others from tracking the websites you visit. Tor attempts to make all users look-alike to stop anybody determining you from the characteristics of your internet browser or devices.

It is made up of sites that are only available through a Tor connection and can not be found through online search engine like Google. The dark web is often related to crooks which is why it's unlawful in some nations. If you wish to use the internet and leave no digital footprint, using the Tor internet browser is the best solution.

You can absolutely utilize Tor for regular web surfing without a VPN. While not strictly restricted in the majority of Western countries, the significant tech market gamers avoid motivating Tor internet browser use.
Using a complimentary VPN service may put your online security at risk. When you utilize a VPN server, you protect your traffic from being monitored by your ISP.
Vpn Vs Tor — Which Is Better?
Tor is a complimentary web browser that will secure your online activity, however it is slower, does not supply access to all sites, and can potentially lead to issues with the law. By Mary Atamaniuk Updated: Jan 21, 2021 15 minutes read Upgraded: Jan 21, 2021 15 min checked out A digital material author passionate about tech, marketing, and cybersecurity.
Our information is a valuable commodity and there are plenty of individuals who would like to get their hands on it, from spouses and marketing teams to crooks and state-sponsored spies. Due to the fact that of that, tools like Tor and Virtual Private Networks (VPNs) are growing in popularity. While both tools can improve your online anonymity, they're as different as apples and orang ...
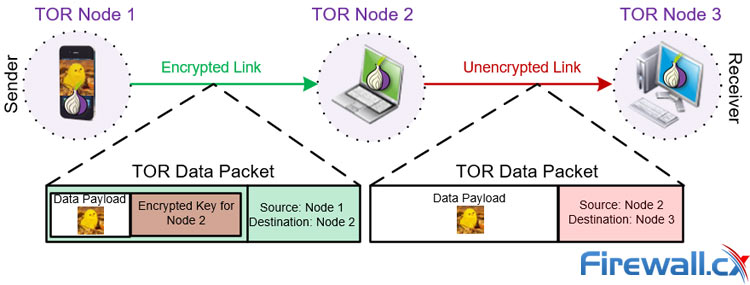
The Tor network can be used to access the regular Internet, web it hides your IP address from everyone, everybody the consisting of operating individuals Tor network itself, or the Dark Web, where everyone's Everybody address is hidden from concealed elseEverybody When you use Tor, your traffic links to the Web through a "Circuit", a collection of three computers, or Tor "nodes" that is altered every 10 minutes.
This prevents anybody from snooping on your it, consisting of the majority of the Tor network itself. Each computer in a Circuit peels back one layer of file encryption, to reveal details that only it can see. They work like this: The is where your traffic enters the Circuit. It can see your IP address and the IP address of the middle node.
Theis where your traffic leaves the Circuit. It can see the IP address of the middle node and your traffic's destination. The Exit Node behaves a bit like a VPN, so any service you utilize on the Web will see the Exit Node's IP address as the source of your traffic.
The most uncomplicated method to use the Tor network is through the Tor Internet browser. All you need to do is download and set up the newest version from the main website and use it like a regular web browser. There is no learning curve; the Tor web browser is based on Firefox and is as easy to utilize as any internet browser.
Tor Vs Vpn: What's The Difference And Which Is Better In ...
Your traffic joins the Web from the VPN service provider and uses your VPN supplier's IP address, so it appears to come from there. Here are some essential distinctions between the two technologies: There are many VPN services to choose from, there is only one Tor network. A VPN assumes you trust your VPN supplier.
Your VPN supplier aims to supply a connection that is quick and steady. VPN service companies are usually run by companies answerable to local laws.
If you have actually ever desired to change your IP address to gain access to material from another place in the world, you've most likely come across proxy servers, VPNs and Tor. This short article will help you choose in between a VPN vs proxy vs Tor to protect your online activity.
A VPN will change your IP address and encrypt your internet connection, providing you the greatest level of security. We'll discuss what those are and how VPNs, proxies and Tor compare.
Tor Vs Vpn: Which One's Better? [Expert's Guide]
Which Is Faster, VPN or Proxy? A VPN will usually be faster than a proxy server if you're using an excellent quality VPN. Does a VPN Bypass a Proxy? A VPN should not bypass a proxy. The VPN client would secure your information and send it to the VPN server, which would then send it to the proxy server.
To that end, we'll explain what proxy servers, VPNs and the Tor network do and how they work. We'll talk about how and when you must utilize them to assist you pick the best service for your usage case. Between a proxy vs VPN vs Tor, it's clear to us that a VPN connection is the fastest and most safe.
Latest Posts
Best Virtual Private Network (Vpn) Software 2023
The Best Vpn For Business In 2023: Top 8 Corporate ...
Best Vpns For Freelancers And Remote Workers: Protect ...